John, a penetration tester from a pen test firm, was asked to collect information about the host file in a Windows system directory. Which of the following is the location of the host file in Window system directory?
Correct Answer:
B
DMZ is a network designed to give the public access to the specific internal resources and you might want to do the same thing for guests visiting organizations without compromising the integrity of the internal resources. In general, attacks on the wireless networks fall into four basic categories.
Identify the attacks that fall under Passive attacks category.
Correct Answer:
A
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet.
The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.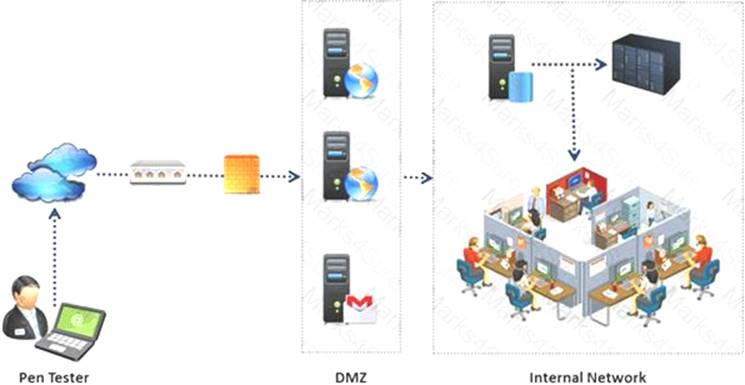
During external penetration testing, which of the following scanning techniques allow you to determine a port’s state without making a full connection to the host?
Correct Answer:
B
You are assisting a Department of Defense contract company to become compliant with the stringent
security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers.
What type of firewall must you implement to abide by this policy?
Correct Answer:
D
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for breaking messages into segments, re-assembling them at the destination station, and re-sending. Which one of the following protocols does not use the TCP?
Correct Answer:
A