Which two characteristics are associated with 802 1s? (Choose two)
Correct Answer:
CE
Refer to the exhibit.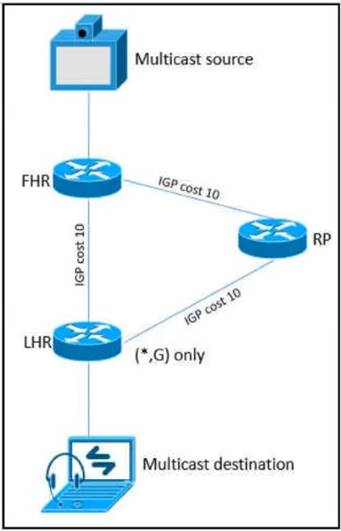
As part of a redesign project, you must predict multicast behavior What happens to the multicast traffic received on the shared tree (*,G), if it is received on the LHR interface indicated*?
Correct Answer:
A
https://www.cisco.com/c/en/us/support/docs/ip/ip-multicast/16450-mcastguide0.html
When a multicast packet arrives on an interface, the RPF process checks to ensure that this incoming interface is the outgoing interface used by unicast routing in order to reach the source of the multicast packet. This RPF check process prevents loops. Multicast routing does not forward a packet unless the source of the packet passes a RPF check. Once a packet passes this RPF check, multicast routing forwards the packet based only upon the destination address.
What are two descriptions of network optimization? (Choose two.)
Correct Answer:
AD
A network architect in an enterprise is designing a network policy for certain database applications. The goal of the policy is to allow these applications to access the internet directly, whereas other user and network applications that communicate with systems or users outside their own network must be routed through the data center. The focus is on achieving higher availability and a better user experience for the database applications, but switching between different network paths based on performance characteristics must be supported.
Which solution meets these requirements?
Correct Answer:
C
https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/sd-wan/nb-06-cloud-onramp-saas-faq-ct
Company XYZ was not satisfied with the reconvergence time OSPF is taking. BFD was implemented to try to reduce the reconvergence time, but the network is still experiencing delays when having to reconverge. Which technology will improve the design?
Correct Answer:
B