- (Exam Topic 3)
Which Cisco DNA Center Intent API action is used to retrieve the number of devices known to a DNA Center?
Correct Answer:
A
- (Exam Topic 3)
An organization wants to secure data in a cloud environment. Its security model requires that all users be authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and data. There is also a need to allow certain application traffic and deny all other traffic by default. Which technology must be used to implement these requirements?
Correct Answer:
C
Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location.The Zero Trust model uses microsegmentation — a security technique that involves dividing perimeters into small zones to maintain separate access to every part of the network — to contain attacks.
- (Exam Topic 3)
Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right.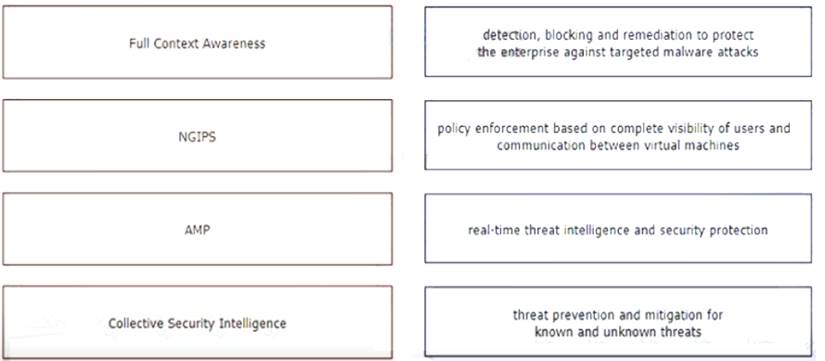
Solution:
Full Context Awareness - policy enforcement NGIPS - threat prevention
AMP - real-time
Collective Sec Intel - Detection, blocking an remediation
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 1)
What is the difference between deceptive phishing and spear phishing?
Correct Answer:
B
In deceptive phishing, fraudsters impersonate a legitimate company in an attempt to steal people’s personal data or login credentials. Those emails frequently use threats and a sense of urgency to scare users into doing what the attackers want.
Spear phishing is carefully designed to get a single recipient to respond. Criminals select an individual target within an organization, using social media and other public information – and craft a fake email tailored for that person.
- (Exam Topic 1)
Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from Cisco and other vendors to share data and interoperate with each other?
Correct Answer:
B
With Cisco pxGrid (Platform Exchange Grid), your multiple security products can now share data and work together. This open, scalable, and IETF standards-driven platform helps you automate security to get answers and contain threats faster.