- (Topic 4)
Which function is performed by vSmart in the Cisco SD-WAN architecture?
Correct Answer:
B
- (Topic 4)
An engineer must use flexible NetFlow on a group of switches. To prevent overloading of the flow collector, if the flow is idle for 20 seconds, the flow sample should be exported. Which command set should be applied?
A)
B)
C)
D)
Correct Answer:
C
Option C is the correct set of commands to apply flexible NetFlow on a group of switches with the given requirement. The configuration steps are as follows12:
✑ Define a flow record that specifies the fields to be collected and exported for the flows. In this case, the flow record is named FNF-RECORD and it collects the source and destination IP addresses, the input and output interfaces, the transport protocol, and the source and destination port numbers: flow record FNF-
RECORD and match ipv4 source address, match ipv4 destination address, match interface input, match interface output, match transport protocol, match transport source-port, match transport destination-port.
✑ Define a flow exporter that specifies the destination and transport protocol for sending the flow data. In this case, the flow exporter is named FNF- EXPORTER and it uses UDP port 9996 to send the flow data to the IP address 10.10.10.10: flow exporter FNF-EXPORTER and destination 10.10.10.10, transport udp 9996.
✑ Define a flow monitor that applies the flow record and the flow exporter to the monitored traffic. In this case, the flow monitor is named FNF-MONITOR and it uses the flow record FNF-RECORD and the flow exporter FNF-EXPORTER. It also sets the cache timeout for inactive flows to 20 seconds, which means that the flow sample will be exported if the flow is idle for 20 seconds: flow monitor FNF-
MONITOR and record FNF-RECORD, exporter FNF-EXPORTER, cache timeout inactive 20.
✑ Apply the flow monitor to the interfaces that need to be monitored. In this case, the flow monitor FNF-MONITOR is applied to the input and output direction of the interface GigabitEthernet0/1: interface GigabitEthernet0/1 and ip flow monitor FNF-MONITOR input, ip flow monitor FNF-MONITOR output.
Option A is incorrect because it does not set the cache timeout for inactive flows to 20 seconds, which is required by the question. The default cache timeout for inactive flows is 15 seconds1.
Option B is incorrect because it does not apply the flow monitor to the output direction of the interface, which is required to capture both incoming and outgoing traffic on the interface1.
Option D is incorrect because it does not use a flow record to specify the fields to be collected and exported for the flows, which is required to customize the flow data according to the user’s needs1. References: 1: Configuring Flexible NetFlow, 2: Flexible NetFlow Configuration Guide
- (Topic 4)
Refer to the exhibit.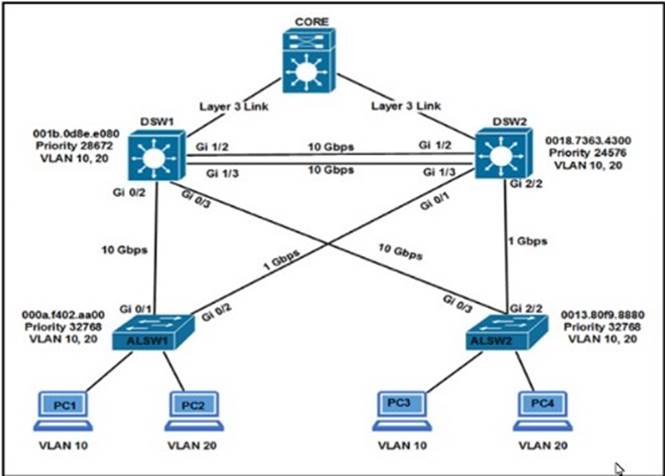
Assuming all links are functional, which path does PC1 take to reach DSW1?
Correct Answer:
B
- (Topic 3)
What is the recommended minimum SNR for data applications on wireless networks?
Correct Answer:
B
Generally, a signal with an SNR value of 20 dB or more is recommended for data networks where as an SNR value of 25 dB or more is recommended for networks that use voice applications https://documentation.meraki.com/MR/WiFi_Basics_and_Best_Practices/Signal-to- Noise_Ratio_(SNR)_and_Wireless_Signal_Strength#:~:text=Generally%2C%20a%20signa l%20with%20an,networks%20that%20use%20voice%20applications.
- (Topic 1)
Refer to the exhibit.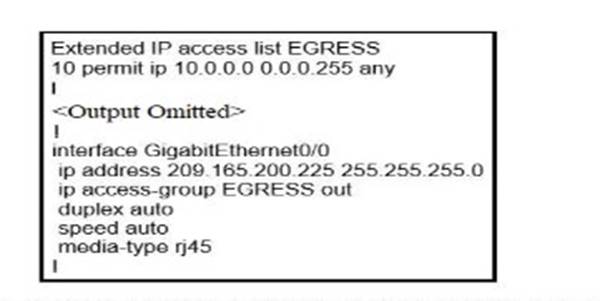
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router However, the router can still ping hosts on the 209.165.200.0/24 subnet. Which explanation of this behavior is true?
Correct Answer:
A