A company’s Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application.
What kind of Web application vulnerability likely exists in their software?
Correct Answer:
A
Which of the following Linux commands will resolve a domain name into IP address?
Correct Answer:
A
Consider the following Nmap output: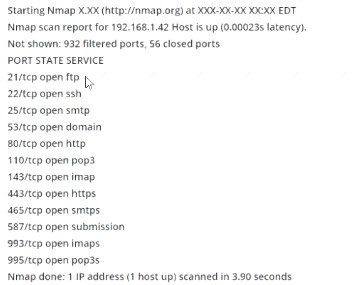
what command-line parameter could you use to determine the type and version number of the web server?
Correct Answer:
A
C:\Users\moi>nmap -h | findstr " -sV" -sV: Probe open ports to determine service/version info
How does a denial-of-service attack work?
Correct Answer:
A
Which of the following is a command line packet analyzer similar to GUI-based Wireshark?
Correct Answer:
B