- (Topic 23)
You receive an e-mail like the one shown below. When you click on the link contained in the mail, you are redirected to a website seeking you to download free Anti-Virus software.
Dear valued customers,
We are pleased to announce the newest version of Antivirus 2010 for Windows which will probe you with total security against the latest spyware, malware, viruses, Trojans and other online threats. Simply visit the link below and enter your antivirus code:
Antivirus code: 5014 http://www.juggyboy/virus/virus.html
Thank you for choosing us, the worldwide leader Antivirus solutions. Mike Robertson
PDF Reader Support
Copyright Antivirus 2010 ?All rights reserved
If you want to stop receiving mail, please go to: http://www.juggyboy.com
or you may contact us at the following address: Media Internet Consultants, Edif. Neptuno, Planta Baja, Ave. Ricardo J. Alfaro, Tumba Muerto, n/a Panama
How will you determine if this is Real Anti-Virus or Fake Anti-Virus website?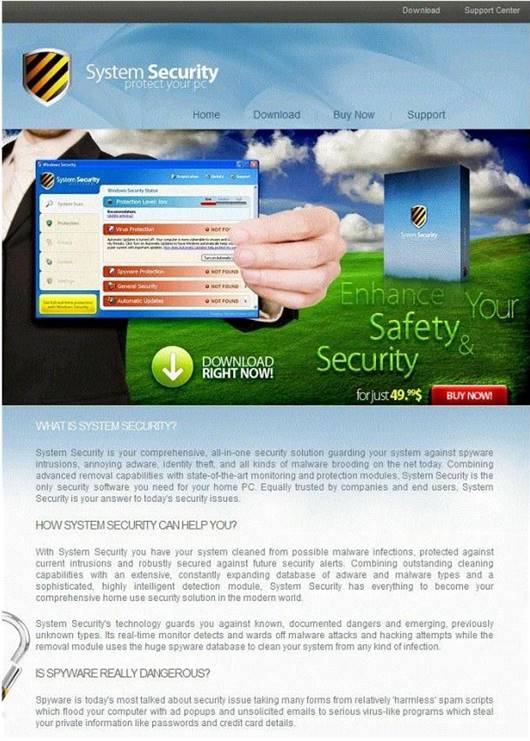
Correct Answer:
C
- (Topic 19)
SSL has been seen as the solution to several common security problems. Administrators will often make use of SSL to encrypt communication from point A to point B. Why do you think this could be a bad idea if there is an Intrusion Detection System deployed to monitor the traffic between point A and B?
Correct Answer:
D
Because the traffic is encrypted, an IDS cannot understand it or evaluate the payload.
- (Topic 5)
Which of the following steganography utilities exploits the nature of white space and allows the user to conceal information in these white spaces?
Correct Answer:
A
The program snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected.
- (Topic 4)
What does FIN in TCP flag define?
Correct Answer:
A
The FIN flag stands for the word FINished. This flag is used to tear down the virtual connections created using the previous flag (SYN), so because of this reason, the FIN flag always appears when the last packets are exchanged between a connection.
- (Topic 23)
You are gathering competitive intelligence on an organization. You notice that they have jobs listed on a few Internet job-hunting sites. There are two jobs for network and system administrators. How can this help you in foot printing the organization?
Correct Answer:
D