An organization is implementing and deploying the SIEM with following capabilities.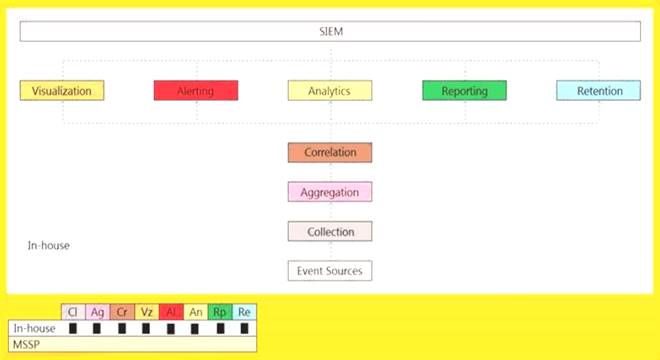
What kind of SIEM deployment architecture the organization is planning to implement?
Correct Answer:
A
A type of threat intelligent that find out the information about the attacker by misleading them is known as.
Correct Answer:
C
Sam, a security analyst with INFOSOL INC., while monitoring and analyzing IIS logs, detected an event matching regex /\w*((%27)|(’))((%6F)|o|(%4F))((%72)|r|(%52))/ix.
What does this event log indicate?
Correct Answer:
A
Which of the following process refers to the discarding of the packets at the routing level without informing the source that the data did not reach its intended recipient?
Correct Answer:
C
Which of the following attack inundates DHCP servers with fake DHCP requests to exhaust all available IP addresses?
Correct Answer:
A