The Malicious code that is installed on the computer without user’s knowledge to acquire information from the user’s machine and send it to the attacker who can access it remotely is called:
Correct Answer:
A
The free, open source, TCP/IP protocol analyzer, sniffer and packet capturing utility standard across many industries and educational institutions is known as:
Correct Answer:
B
The flow chart gives a view of different roles played by the different personnel of CSIRT. Identify the incident response personnel denoted by A, B, C, D, E, F and G.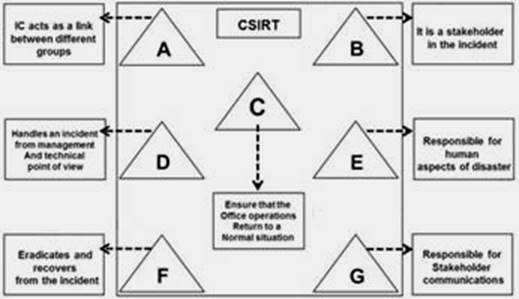
Correct Answer:
C
Except for some common roles, the roles in an IRT are distinct for every organization. Which among the following is the role played by the Incident Coordinator of an IRT?
Correct Answer:
B
Which of the following may be considered as insider threat(s):
Correct Answer:
B