Refer to the exhibit.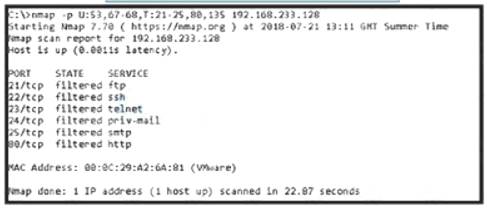
An attacker scanned the server using Nmap. What did the attacker obtain from this scan?
Correct Answer:
C
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Correct Answer:
D
Refer to the exhibit.
Which type of log is displayed?
Correct Answer:
A
You also see the 5-tuple in IPS events, NetFlow records, and other event data. In fact, on the exam you may need to differentiate between a firewall log versus a traditional IPS or IDS event. One of the things to remember is that traditional IDS and IPS use signatures, so an easy way to differentiate is by looking for a signature ID (SigID). If you see a signature ID, then most definitely the event is a traditional IPS or IDS event.
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
Correct Answer:
C
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
Correct Answer:
D