Which attack method intercepts traffic on a switched network?
Correct Answer:
B
An ARP-based MITM attack is achieved when an attacker poisons the ARP cache of two devices with the MAC address of the attacker's network interface card (NIC). Once the ARP caches have been successfully poisoned, each victim device sends all its packets to the attacker when communicating to the other device and puts the attacker in the middle of the communications path between the two victim devices. It allows an attacker to easily monitor all communication between victim devices. The intent is to intercept and view the information being passed between the two victim devices and potentially introduce sessions and traffic between the two victim devices
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
Correct Answer:
D
Which event is user interaction?
Correct Answer:
D
Refer to the exhibit.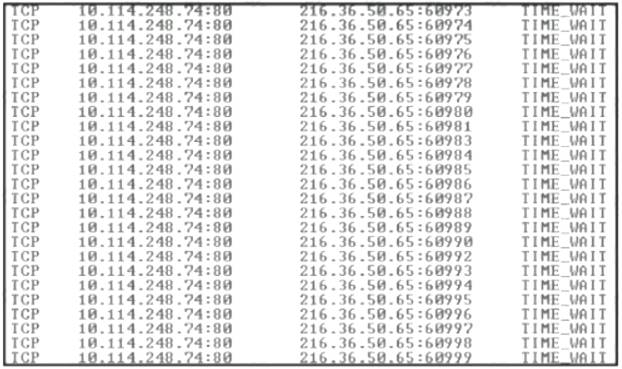
An engineer received a ticket about a slowed-down web application The engineer runs the #netstat -an command. How must the engineer interpret the results?
Correct Answer:
C
Refer to the exhibit.
Which type of attack is being executed?
Correct Answer:
A