Drag and drop the security concept from the left onto the example of that concept on the right.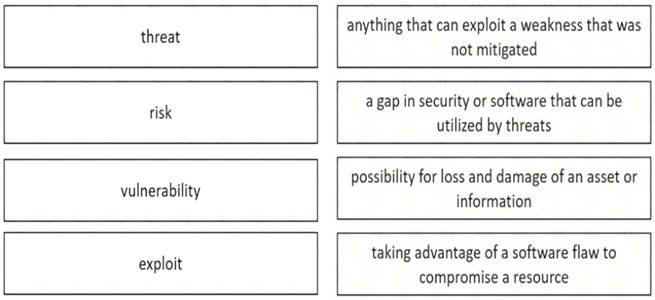
Solution:
Table Description automatically generated
Does this meet the goal?
Correct Answer:
A
Refer to the exhibit.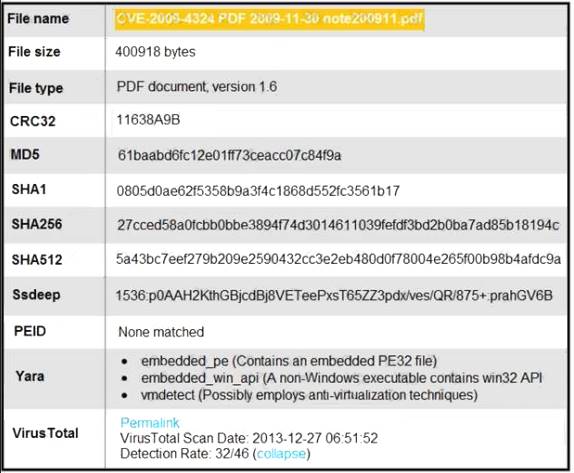
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
Correct Answer:
C
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
Correct Answer:
BE
Refer to the exhibit.
Which field contains DNS header information if the payload is a query or a response?
Correct Answer:
B
Refer to the exhibit.
Which component is identifiable in this exhibit?
Correct Answer:
C
https://docs.microsoft.com/en-us/windows/win32/sysinfo/registry-hives https://ldapwiki.com/wiki/HKEY_LOCAL_MACHINE#:~:text=HKEY_LOCAL_MACHINE%20Windows%2