An automotive company provides new types of engines and special brakes for rally sports cars. The company has a database of inventions and patents for their engines and technical information Customers can access the database through the company's website after they register and identify themselves. Which type of protected data is accessed by customers?
Correct Answer:
B
Which HTTP header field is used in forensics to identify the type of browser used?
Correct Answer:
C
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:12.0) Gecko/20100101 Firefox/12.0 In computing, a user agent is any software, acting on behalf of a user, which "retrieves, renders and facilitates end-user interaction with Web content".[1] A user agent is therefore a special kind of software agent. https://en.wikipedia.org/wiki/User_agent#User_agent_identification
A user agent is a computer program representing a person, for example, a browser in a Web context. https://developer.mozilla.org/en-US/docs/Glossary/User_agent
How does TOR alter data content during transit?
Correct Answer:
B
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Correct Answer:
CD
The following are some factors that are used during attribution in an investigation: Assets, Threat actor, Indicators of Compromise (IoCs), Indicators of Attack (IoAs), Chain of custody Asset: This factor identifies which assets were compromised by a threat actor or hacker. An example of an asset can be an organization's domain controller (DC) that runs Active Directory Domain Services (AD DS). AD is a service that allows an administrator to manage user accounts, user groups, and policies across a Microsoft Windows environment. Keep in mind that an asset is anything that has value to an organization; it can be something physical, digital, or even people. Cisco Certified CyberOps Associate 200-201 Certification Guide
Refer to the exhibit.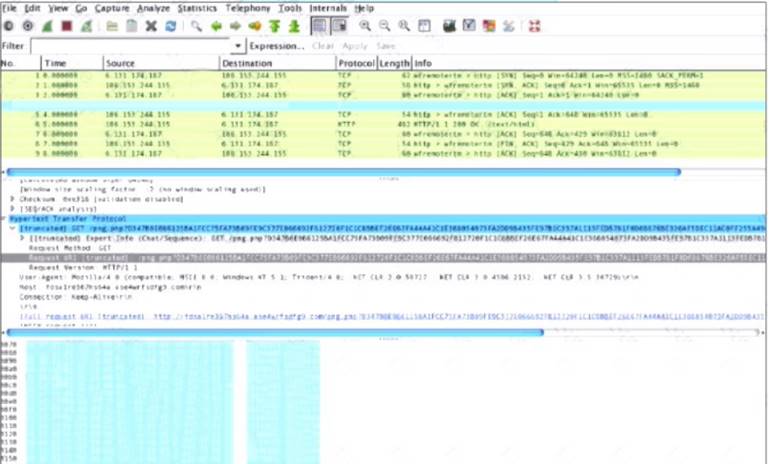
What is shown in this PCAP file?
Correct Answer:
D