What is the practice of giving an employee access to only the resources needed to accomplish their job?
Correct Answer:
A
What is a difference between tampered and untampered disk images?
Correct Answer:
D
The disk image must be intact for forensics analysis. As a cybersecurity professional, you may be given the task of capturing an image of a disk in a forensic manner. Imagine a security incident has occurred on a system and you are required to perform some forensic investigation to determine who and what caused the attack. Additionally, you want to ensure the data that was captured is not tampered with or modified during the creation of a disk image process. Ref: Cisco Certified CyberOps Associate 200-201 Certification Guide
Refer to the exhibit.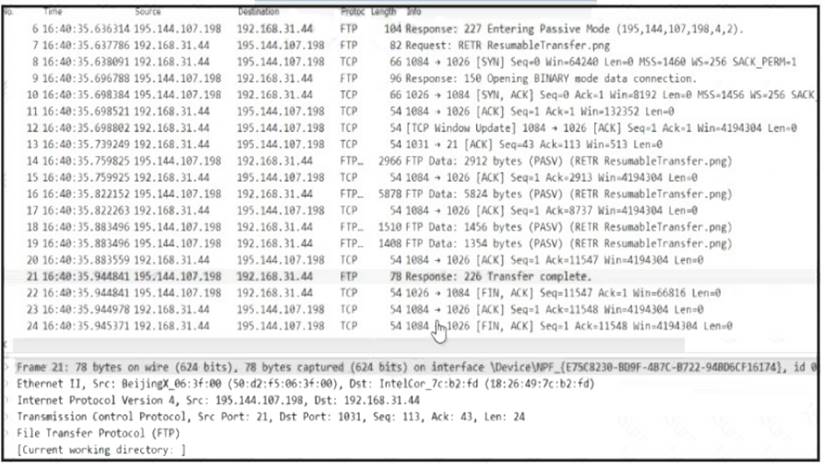
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
Correct Answer:
B
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
Correct Answer:
CE
What specific type of analysis is assigning values to the scenario to see expected outcomes?
Correct Answer:
A