Which system monitors local system operation and local network access for violations of a security policy?
Correct Answer:
A
HIDS is capable of monitoring the internals of a computing system as well as the network packets on its network interfaces. Host-based firewall is a piece of software running on a single Host that can restrict incoming and outgoing Network activity for that host only.
Refer to the exhibit.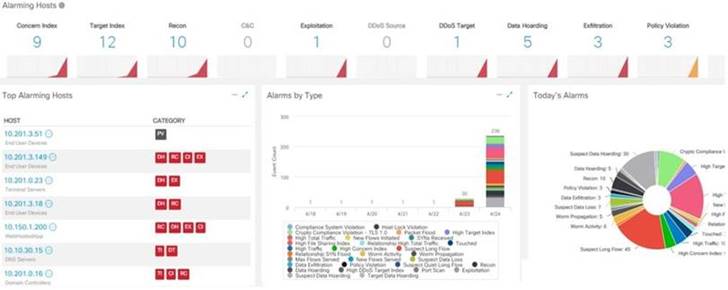
What is the potential threat identified in this Stealthwatch dashboard?
Correct Answer:
C
"EX" = exfiltration And there are three.
Also the "suspect long flow" and "suspect data heading" suggest, for example, DNS exfiltration
https://www.cisco.com/c/dam/en/us/td/docs/security/stealthwatch/management_console/smc_users_guide/SW_6 page 177.
Which category relates to improper use or disclosure of PII data?
Correct Answer:
C
What is a difference between SIEM and SOAR?
Correct Answer:
B
Refer to the exhibit.
Which type of log is displayed?
Correct Answer:
B