According to the September 2020 threat intelligence feeds a new malware called Egregor was introduced and used in many attacks. Distnbution of Egregor is pnmanly through a Cobalt Strike that has been installed on victim's workstations using RDP exploits Malware exfiltrates the victim's data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
Correct Answer:
B
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Correct Answer:
C
Refer to the exhibit.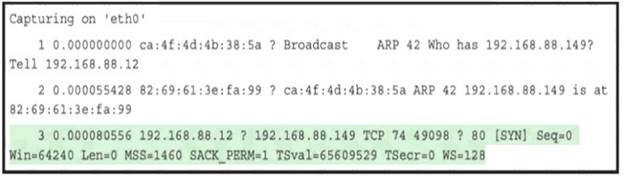
What must be interpreted from this packet capture?
Correct Answer:
B
Which information must an organization use to understand the threats currently targeting the organization?
Correct Answer:
A
Drag and drop the elements from the left into the correct order for incident handling on the right.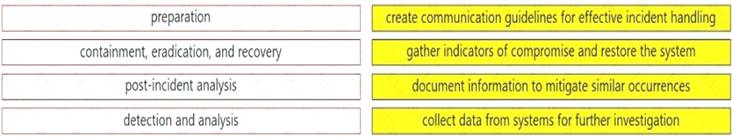
Solution: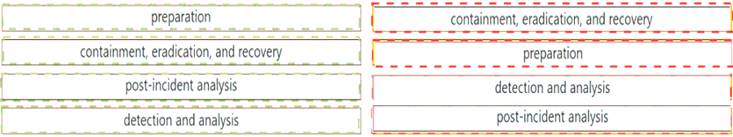
Does this meet the goal?
Correct Answer:
A