_________ content type supports sending NITRO commands to NetScaler. (Choose the correct option to complete sentence.)
Correct Answer:
B
Scenario: A Citrix Architect needs to assess an existing NetScaler Gateway deployment. During the assessment, the architect collected key requirements for VPN users, as well as the current session profile settings that are applied to those users.
Click the Exhibit button to view the information collected by the architect.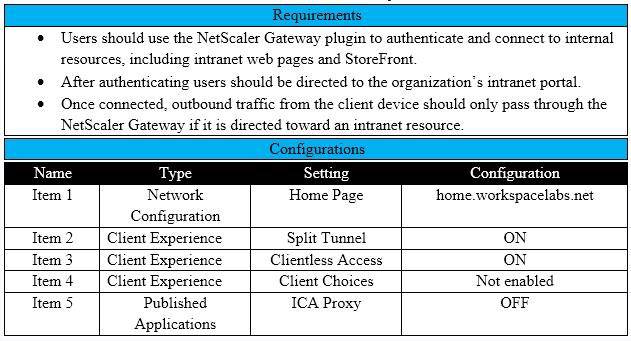
Which configurations should the architect change to meet all the stated requirements?
Correct Answer:
E
Scenario: A Citrix Architect needs to deploy SAML integration between NetScaler (Identity Provider) and ShareFile (Service Provider). The design requirements for SAML setup are as follows:
* NetScaler must be deployed as the Identity Provider (IDP).
* ShareFile server must be deployed as the SAML Service Provider (SP).
* The users in domain workspacelab.com must be able to perform Single Sign-on to ShareFile after authenticating at the NetScaler.
* The User ID must be UserPrincipalName.
* The User ID and Password must be evaluated by NetScaler against the Active Directory servers SFO-ADS-001 and SFO-ADS-002.
* After successful authentication, NetScaler creates a SAML Assertion and passes it back to ShareFile.
* Single Sign-on must be performed. SHA 1 algorithm must be utilized.
The verification environment details are as follows:
* Domain Name: workspacelab.com
* NetScaler AAA virtual server URL https://auth.workspacelab.com
* ShareFile URL https://sharefile.workspacelab.com
Which SAML IDP action will meet the design requirements?
Correct Answer:
C
Which step does a Citrix Architect need to ensure during the Define phase when following the Citrix Methodology?
Correct Answer:
E
Reference: https://www.slideshare.net/davidmcg/designing-your-xenapp-75-environment
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy settings.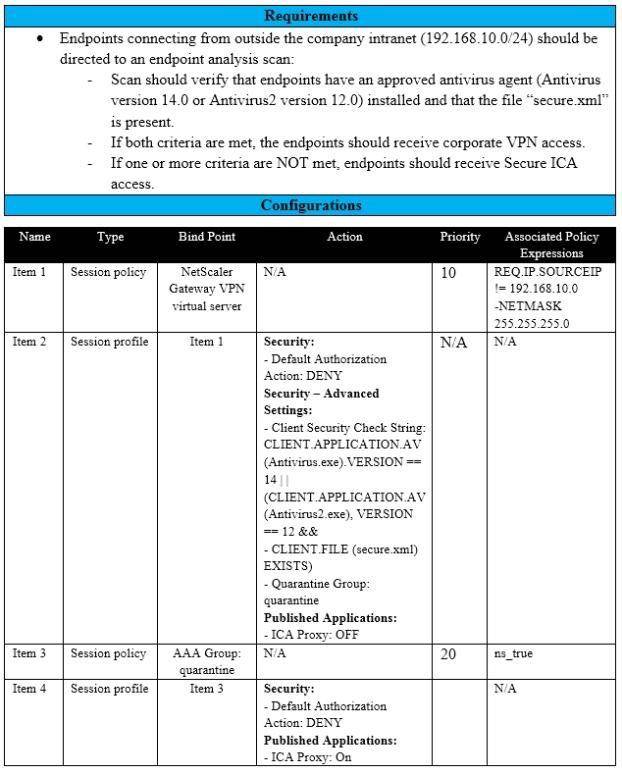
Which setting is preventing the security requirements of the organization from being met?
Correct Answer:
D